In today’s interconnected world, where data flows like a river, the concept of proxy ports may seem like just another drop in the ocean. Yet, these ports are the gateways that control and direct the flow of data, ensuring it reaches its destination securely and efficiently. Whether you’re a tech enthusiast, an IT professional, or simply curious about how the internet works, understanding proxy ports is crucial. This guide will take you on a journey through the world of proxy ports, explaining what they are, how they function, and why they’re essential.
What is a Proxy Port?
A proxy port is a specific endpoint on a proxy server that facilitates communication between your device and the internet. Think of it as a digital post office, where each port is a unique mailbox handling different types of data. When you configure a proxy server, you provide an IP address and a port number. The IP address directs the data to the correct server, while the port number specifies the service on that server responsible for handling the data.
Common Proxy Ports
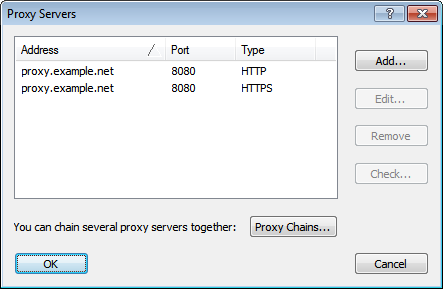
- HTTP Proxies: Typically use port 8080 or 3128. These ports handle standard web traffic, allowing you to browse websites with ease.
- HTTPS Proxies: Use port 443, ensuring secure, encrypted communication for sensitive transactions like online banking.
- SOCKS Proxies: Operate on port 1080, providing a versatile solution for various types of internet traffic, including video streaming and gaming.
How Does a Proxy Port Work?
1. Data Request Initiation
Imagine you’re sending a letter. Instead of mailing it directly to the recipient, you send it to a middleman (the proxy server). This middleman receives your request, which includes the proxy server’s IP address and the designated proxy port.
2. Data Transmission through the Proxy Port
Once the proxy server receives your request, it listens for incoming data on the specified port. This process is akin to a receptionist directing calls to the right department. The server processes the request, which might involve forwarding it to the intended destination or modifying the data for security purposes.
3. Response Handling
After the proxy server receives a response from the destination server, it sends the data back to your device through the same proxy port. This ensures a consistent and secure communication channel, like a two-way street where traffic flows smoothly in both directions.
4. Port Forwarding and Security
Proxy ports can also be used for port forwarding, redirecting communication from one port to another. This enhances security by masking the true destination of the data or balancing network loads across multiple servers. It’s like using a secret passageway to reach your destination, keeping your route hidden from prying eyes.
5. Protocol Support
Proxy ports support various protocols such as HTTP, HTTPS, and SOCKS. Each protocol has its own set of ports and rules for handling data. For example, HTTP proxies usually operate on port 80, while HTTPS proxies use port 443 for secure communications.
Why Use a Proxy Port?
Anonymity and Privacy
Routing your internet traffic through a proxy server masks your IP address, providing anonymity and protecting your privacy. It’s like wearing a digital disguise, making it harder for websites to track your online activities.
Access Control
Proxy ports can be configured to restrict or allow access to specific websites or services, useful for parental controls or workplace internet usage policies. This is akin to having a bouncer at the door, ensuring only authorized guests can enter.
Performance Optimization
Some proxy servers cache data, reducing load times and improving the speed of internet access. This is like having a fast lane on the highway, allowing you to bypass traffic and reach your destination quicker.
Security
Proxies filter malicious content and prevent unauthorized access to your network by acting as a barrier between your internal network and the external internet. Think of it as a digital moat, protecting your castle from invaders.
Practical Cases of Proxy Port Usage
1. Corporate Networks
In corporate environments, proxy ports are often used to control and monitor employee internet usage. By routing all traffic through a proxy server, organizations can enforce security policies, block access to harmful websites, and ensure compliance with regulations.
2. Content Delivery Networks (CDNs)
CDNs use proxy ports to deliver content efficiently to users around the world. By caching data on proxy servers located closer to users, CDNs reduce latency and improve the user experience. This is crucial for streaming services, where fast and reliable data delivery is essential.
3. Online Privacy Tools
Privacy-conscious individuals use proxy ports to anonymize their internet activities. Tools like VPNs and Tor rely on proxy servers to hide users’ IP addresses, making it difficult for third parties to track their online behavior.
The Role of Proxy302 in Enhancing Proxy Port Functionality
Proxy302 is a leading provider of global premium proxy services, offering a flexible, pay-as-you-go model without tiered pricing. With features like high-speed data transmission, robust security, and seamless integration, Proxy302 enhances the functionality of proxy ports, making them more efficient and reliable.
Key Features of Proxy302
- Global Coverage: Access proxy servers in over 100 countries, ensuring fast and reliable connections wherever you are.
- Flexible Pricing: Pay only for what you use, with no hidden fees or tiered pricing structures.
- Free Trial: Test the service with a free trial, experiencing the benefits of Proxy302 before committing.
Understanding proxy ports is essential for effectively configuring and using proxy servers. They are vital in directing internet traffic, ensuring security, and enhancing privacy. By managing data flow through specific ports, proxy servers offer numerous benefits, from improved security to faster internet access. Whether for personal privacy or network management, knowing how proxy ports function is key to leveraging this technology.
Ready to experience the benefits of a premium proxy service? 👉 Start Your Free Trial Now 👈 and discover how a flexible, global proxy solution can enhance your internet experience. Sign up today and take control of your online privacy and security!









3 comments
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.